Information Security Risk Hunt Training
Train your employees to recognize information security threats in realistic scenarios before a real data breach happens
What is Information Security Risk Hunt Training?
This is hands-on security risk awareness, not just rules explained in a presentation
RoT STUDIO’s Information Security Risk Hunt Training is a VR-based learning module designed to help employees actively recognize and respond to information security risks in everyday work scenarios.
Rather than memorizing policies, participants navigate realistic office and digital environments, identify risky behaviors, and make decisions that directly impact data protection and organizational security.
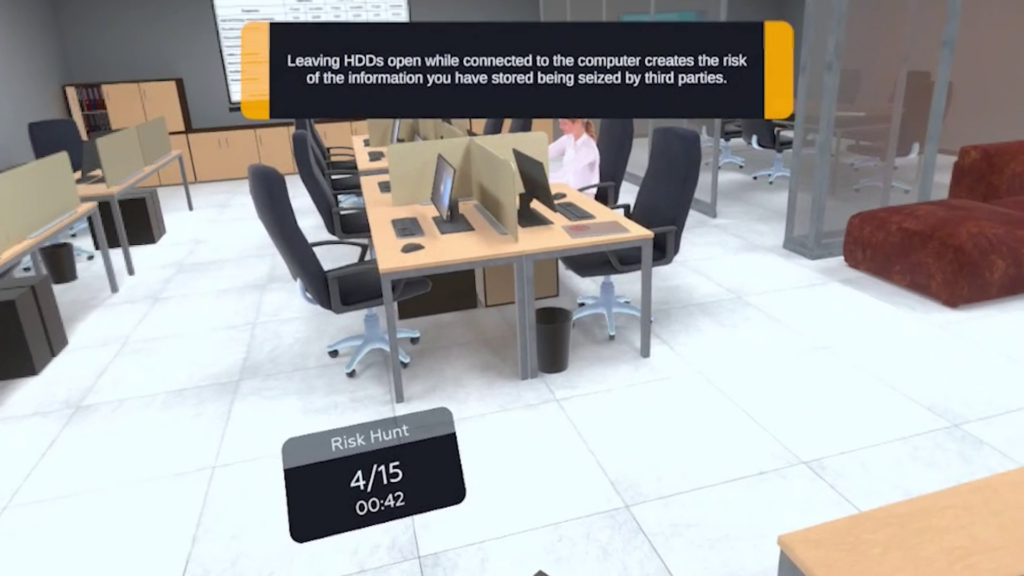
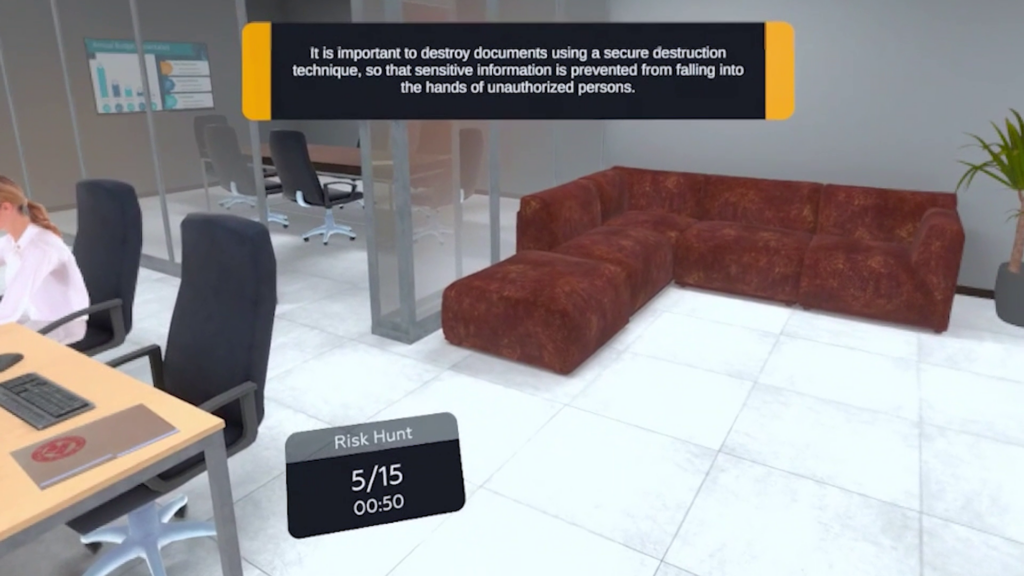
From unsecured screens and weak passwords to social engineering attempts and careless data handling, this training prepares employees to spot risks early and act responsibly before damage occurs.

Whis This Matters Now?
Most information security incidents are not caused by technology,
they are caused by human behavior.
Traditional awareness trainings often explain what not to do, but fail to build real-world reflexes.
Without realistic practice, organizations face:
Traditional Information Security Training:
❌ Policy-focused, mostly theoretical
⚠️ Employees know the rules but miss real threats
💤 Low engagement and fast knowledge decay
👥 Same content for every role and risk level
⏳ No safe way to experience the impact of mistakes
Information Security Training in Virtual Reality:
Scenario-based risk identification training ✅
Spot security threats in realistic work situations 👀
Immediate feedback on risky and safe decisions 🎯
Measure awareness levels and behavior patterns 📊
Safe repetition until secure behavior becomes a habit 🔁
How It Works?
Simple ● Smart ● Scalable
Step into VR
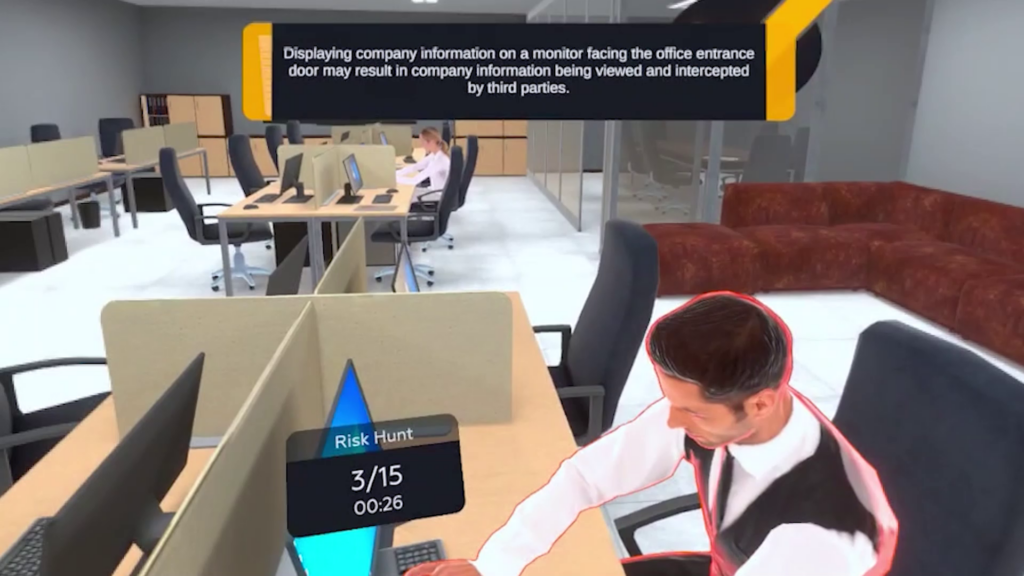
Learners enter a virtual workplace environment where realistic information security risks are embedded into daily tasks
Hunt for Security Risks
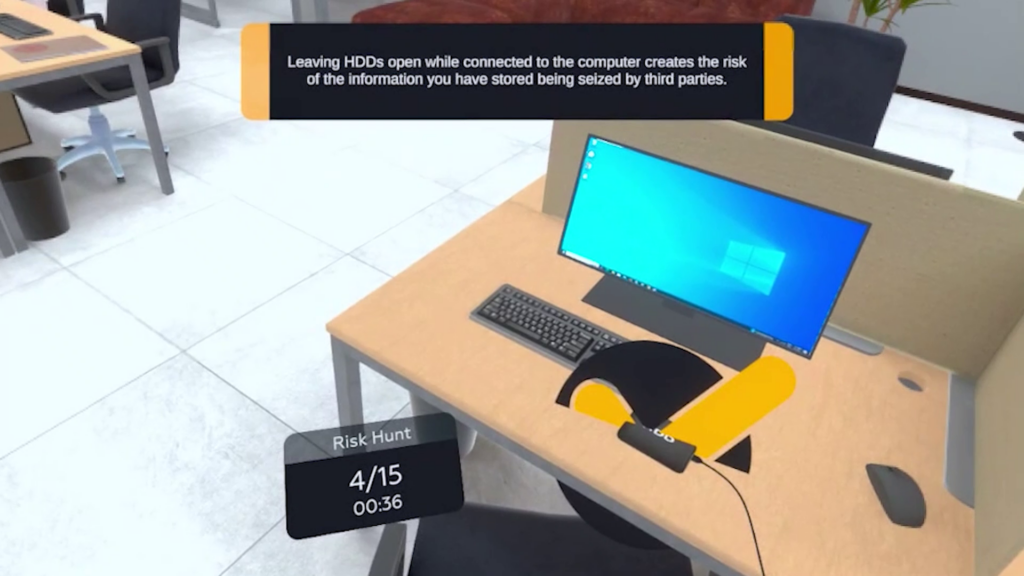
Participants identify risks such as unsecured devices, weak passwords, phishing attempts, data leaks, and policy violations
Make Decisions
Users choose how to react in each situation, learning the consequences of safe and unsafe actions
Review & Improve
Performance reports highlight risky behaviors, decision patterns, and improvement areas for targeted follow-up training
Key Benefits
Real Information Security Outcomes Your Organization Needs
Skills Your Team Will Gain
🔍 Identifying information security risks in daily work
🔐 Applying secure data handling and access practices
📧 Recognizing phishing and social engineering attempts
🧩 Understanding the impact of human behavior on security
🚨 Responding correctly to potential security incidents



Who Can Benefit?
Built for Organizations Where Information Security Matters
Trusted By Top Organizations























Cem Pekcan
Business Development Europe Representative
Hello, I am Cem! I work as the Business Development Europe Representative at RoT STUDIO. You can contact me using the information below if you have any questions or want to work with us!
Contact Us!